How 24/7 monitoring enhances business continuity

Naren Ravilla
Founder & CEO
Introduction
Downtime is a costly mistake to experience in this increasingly reliant digital age. A single system outage leads to significant financial losses, damaged reputations, and loss of customer trust. To prevent these disruptions, we use 24/7 monitoring as a vital component for your business continuity.
What is 24/7 monitoring?
24/7 monitoring is a proactive system management approach involving continuous surveillance of IT infrastructure, applications, platforms, and network performance. It employs advanced tools and techniques to detect anomalies, potential threats, and performance bottlenecks. By identifying and addressing issues promptly, 24/7 monitoring ensures optimal system uptime and business continuity.
Why is 24/7 monitoring important?
Quick Response to Threats
- Detects cyberattacks early, such as DDoS attacks, malware infections, and phishing attempts.
- Monitors cloud environments to identify unusual activity, unauthorized access, and compliance violations.
- Prevents data breaches by identifying and addressing vulnerabilities promptly.
- Protects sensitive information by implementing robust security measures tailored for hybrid and cloud-based infrastructures.
Real-Time NOC and SOC Monitoring
- Network Operations Centers (NOCs) monitor and manage the health of IT infrastructure, ensuring stable performance, quick fault resolution, and optimal resource utilization.
- Security Operations Centers (SOCs) focus on identifying and mitigating security threats, ensuring compliance with regulatory standards, and safeguarding sensitive data.
- Coordinated escalation processes ensure that any detected anomaly is routed to the appropriate team for timely resolution.
- Regular reporting and trend analysis by NOC and SOC teams provide actionable insights to prevent future issues.
How Does 24/7 Monitoring Work?
- Real-time Alerts: Receive instant notifications about potential issues, such as system failures, performance degradations, and security threats.
- Automated Responses: Some systems can automatically fix minor problems, such as restarting failed services or applying security patches.
- Data Analysis: Analyze system logs and performance metrics to identify trends, anomalies, and potential future problems.
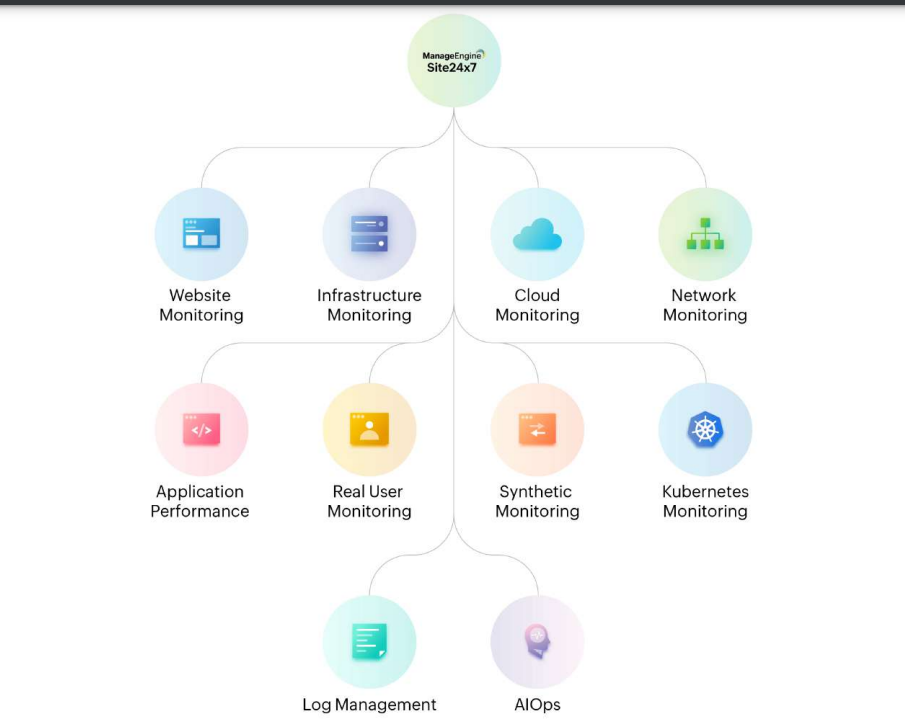
- Key Components:
- Network Monitoring: Monitors network performance, including bandwidth utilization, latency, and packet loss.
- Server Monitoring: Tracks server health, CPU usage, memory consumption, and disk space.
- Application Performance Monitoring (APM): Monitors the performance of web applications, databases, and other critical software.
- Security Monitoring: Detects and responds to security threats, such as unauthorized access attempts, malware infections, and data breaches.
- Log Management: Collects, analyzes, and stores system logs to identify potential issues and security threats.
Best Practices for Effective 24/7 Monitoring
NOC Metrics for Optimal Performance
- Define clear and measurable NOC metrics, such as Mean Time to Detect (MTTD), Mean Time to Resolve (MTTR), and network availability percentages
- Track trends in incident volumes and resolution times to identify areas for improvement
Advanced Alerting and Integration with ITSM Tools
- Implement advanced monitoring solutions that integrate seamlessly with IT Service Management (ITSM) tools, such as ServiceNow, Jira, or BMC Helix
- Use predictive analytics to identify and prioritize critical issues before they escalate
- Ensure notifications are routed to the appropriate teams via multiple channels, including email, SMS, and collaboration platforms like Slack or Microsoft Teams
Skilled Monitoring Teams
- Employ a mix of specialized professionals, including NOC engineers, DevOps teams, and Site Reliability Engineers (SREs), to handle complex monitoring tasks and escalations
- Facilitate collaboration between monitoring teams and business units to ensure alignment with organizational objectives
- Provide ongoing training for teams to stay updated with the latest tools and techniques
Regular Testing and Maintenance
- Regular testing of monitoring tools and processes is conducted to ensure their reliability and accuracy
- Schedule routine maintenance to update systems, patch vulnerabilities, and refine alert configurations
Continuous Improvement
- Evaluate monitoring strategies regularly to address evolving business needs and emerging threats
- Automate repetitive tasks like log analysis and routine checks to enhance efficiency and minimize human error
Strong Password Policies and Access Controls
- Enforce robust password policies and implement multi-factor authentication to protect against unauthorized access
Employee Training and Awareness
- Train employees on security best practices and how to recognize phishing attempts
Incident Response Planning
- Develop a comprehensive incident response plan to guide actions during security breaches or system failures
Real-world example:
A leading e-commerce company implemented a robust 24/7 monitoring solution to ensure seamless operations during peak shopping seasons. By proactively identifying and addressing performance bottlenecks, they could avoid system failures and maintain an excellent customer experience.
Conclusion
In today’s interconnected world, 24/7 monitoring is an indispensable tool for businesses of all sizes. Proactively identifying and addressing issues helps organizations maintain business continuity, improve customer satisfaction, and safeguard their reputation.
By investing in a robust 24/7 monitoring solution and following best practices, businesses minimize downtime, reduce costs, and achieve long-term success.

