
Addressing the Complexity of Cloud Security: Common Threats and the Path Forward

Naren Ravilla
Founder & CEO
Introduction
As organizations continue to migrate to the cloud, the benefits of scalability and flexibility are clear. However, this shift brings a new set of security challenges. Cloud-related security incidents are on the rise, and each additional tool or application introduced to secure cloud environments inadvertently increases complexity—and, often, risk.
In this blog, we explore the most common cloud security incidents, hidden risks of adding more security tools, and strategies for maintaining a strong, streamlined cloud security posture.
The Most Common Cloud-Related Security Incidents
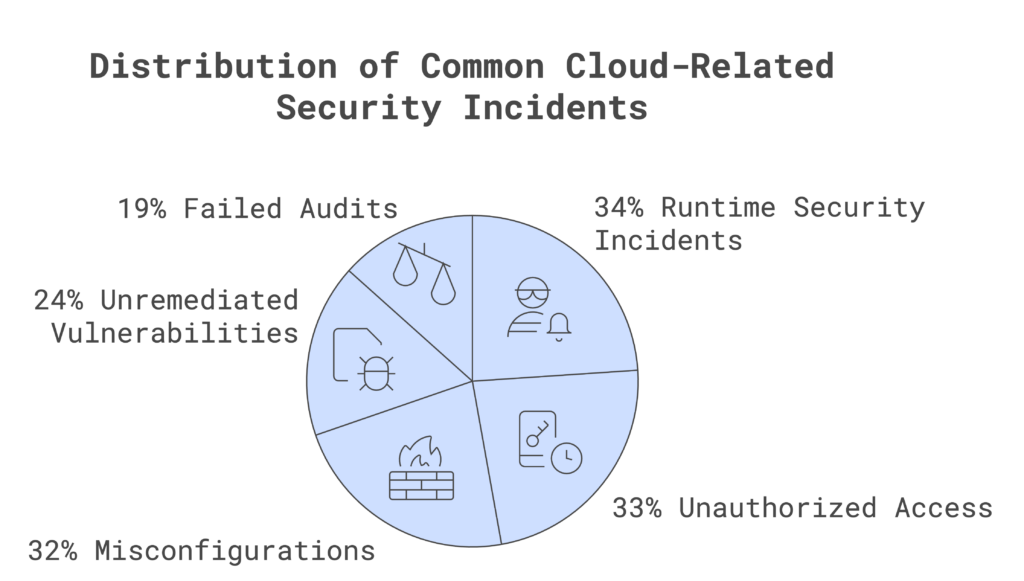
According to data from recent customer research, the following are the most common cloud-related security incidents:
- Security Incidents During Runtime: Runtime security incidents are among the most frequent issues. These can include unauthorized changes to applications, malware, or other types of attacks that occur while systems are actively running. Runtime incidents are especially challenging to detect, as attackers often exploit vulnerabilities in real time without leaving obvious traces.
- Unauthorized Access: Unauthorized access is a major concern as organizations open access points for cloud environments. This security incident could happen due to weak access controls, insufficient multi-factor authentication (MFA), or improper permissions configuration. Unauthorized access can lead to data breaches, loss of sensitive information, and severe reputational damage.
- Misconfigurations: Misconfigurations remain one of the leading causes of cloud security incidents. It often results from human error when setting up security controls, such as improperly configured storage buckets, overly permissive access, or inadequate encryption settings. Even a small configuration error can expose an organization to substantial risk.
- Unremediated Vulnerabilities:
Unremediated vulnerabilities are another common and dangerous type of security incident. Often, these vulnerabilities sprout from outdated software or unpatched systems. Attackers frequently target known vulnerabilities, so addressing these weaknesses before they become an open invitation for breaches is crucial.
- Failed Audits:
Failing security audits is not only a compliance issue but also an indicator of potential security weaknesses. Audit failures often reveal gaps in processes, insufficient documentation, or non-compliance with regulatory standards. Failure to pass an audit can lead to fines, legal implications, and trust issues with customers and stakeholders.
The Impact of Complexity on Cloud Security
With various types of security incidents, it may seem tempting to add more security tools to avoid any potential attack on your organization. It may seem like the right choice, but each tool or application added to the ecosystem introduces its own set of complexities and potential blind spots. This increasing complexity can affect cloud security in several ways.
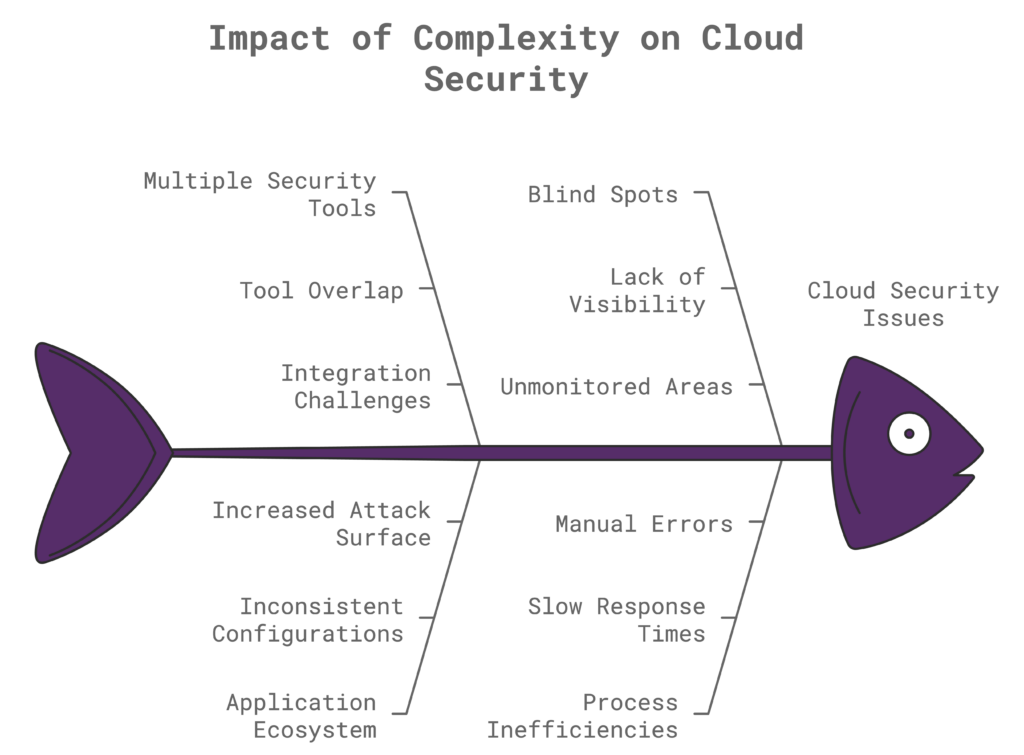
With various types of security incidents, it may seem tempting to add more security tools to avoid any potential attack on your organization. It may seem like the right choice, but each tool or application added to the ecosystem introduces its own set of complexities and potential blind spots. This increasing complexity can affect cloud security in several ways.
- Increased overhead: As organizations add more security tools, managing them becomes increasingly difficult. The sheer volume of alerts and data generated can overwhelm security teams, leading to alert fatigue and slower response times.
- Blind spots and gaps: Integrating multiple security solutions can create gaps or inconsistencies in coverage. Some tools overlap in function, while others leave certain assets unprotected, making it difficult to maintain a cohesive security posture.
- Data silos: Security data scattered across multiple tools can result in silos, making it challenging to get a unified view of potential threats. These silos can prevent teams from connecting the dots, allowing malicious activities to go undetected.
There is a paradox here. Even though adding more security tools is intended to improve security, the outcome can be the opposite. The key is to balance between coverage and simplicity.
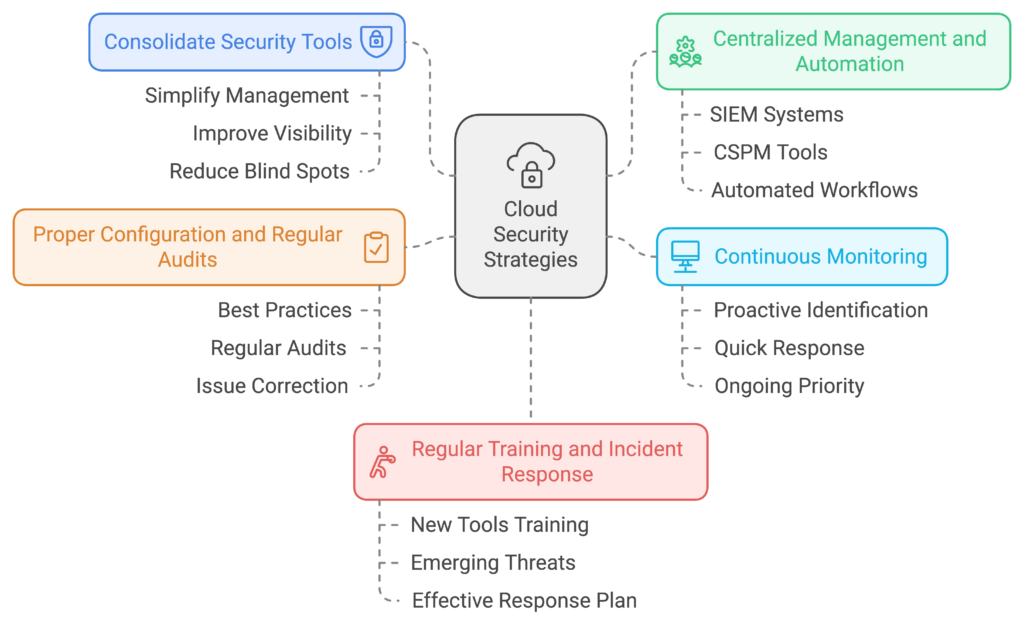
Strategies to Address Cloud Security Complexity
There are various proven strategies to address the rising complexity and simultaneously improve cloud security. Here are a few that we use:

- Consolidate security tools: Using fewer, more integrated tools can simplify management, improve visibility, and reduce the potential for blind spots. Many security platforms offer comprehensive features that reduce the need for multiple overlapping tools.
- Implement centralized management and Automation: Cloud-native solutions, such as Security Information and Event Management (SIEM) systems and Cloud Security Posture Management (CSPM) tools, offer centralized views and automated workflows. Automation can help reduce human error and increase efficiency.
- Adopt continuous monitoring: Continuous monitoring is essential for quickly identifying runtime incidents and responding to unauthorized access. Being proactive with this approach ensures that security is an ongoing priority rather than a periodic check.
- Focus on proper configuration and Regular audits: Misconfigurations are one of the most preventable sources of risk. Implementing best practices for configuration and conducting regular audits can help catch and correct issues before they escalate.
- Regular training and Incident response: Security teams need regular training on new tools and emerging threats. A well-practiced incident response plan ensures the team can act quickly and effectively when incidents occur.
Best Practices for Maintaining a Strong Cloud Security Posture
If you’re looking to strengthen your security posture further, here are a few additional best practices:
- Risk assessment and Prioritization: Conduct regular risk assessments to understand which vulnerabilities pose the greatest threat. Prioritize your remediation efforts based on risk to ensure that you address the most critical issues first.
- Patch management and Vulnerability scanning: Keep software and systems updated with the latest patches, and use vulnerability scanning tools to identify weaknesses in real time.
- Access control and Least privilege policies: Implement strong access controls and limit permissions to only those who need them. These actions reduce the risk of unauthorized access and minimize the potential damage if credentials are compromised.
Conclusion
As cloud security continues to evolve, organizations must adapt by finding the right balance between adding security tools and managing complexity. A streamlined, well-integrated approach to cloud security can enhance visibility, improve efficiency, and ultimately reduce the risk of incidents. This balanced approach is the key to maintaining and strengthening your cloud security.

