High Availability & Secure Infrastructure with Azure: A Step-by-Step Guide

Naren Ravilla
Founder & CEO
Introduction
High availability is a critical requirement for ensuring that applications remain resilient and performant in an increasingly cloud-native world. This blog details the best practices of how a highly available infrastructure can be designed and implemented using Azure native services.
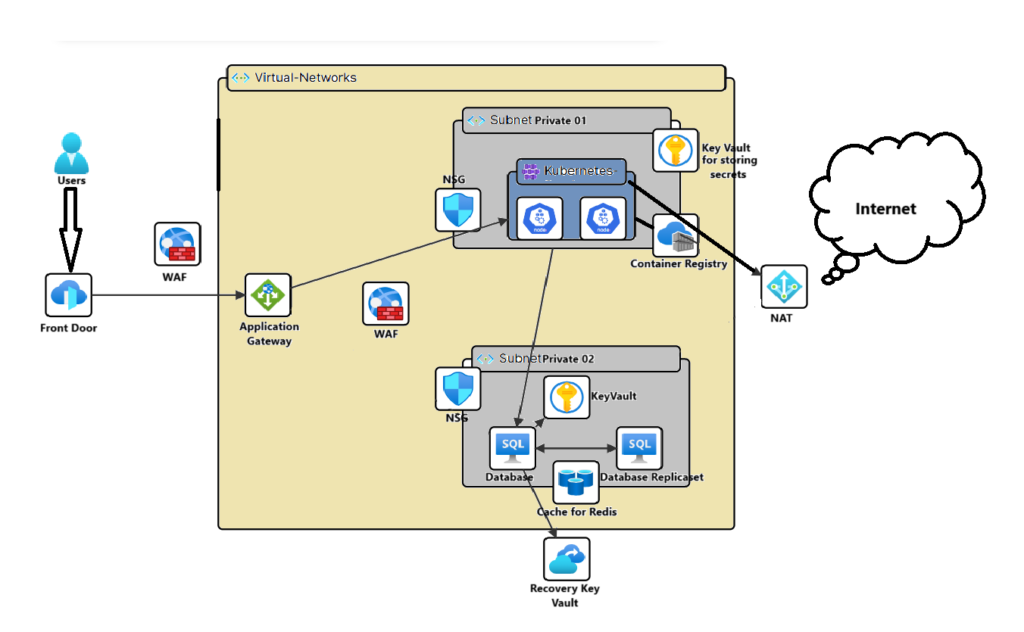
Global Load Balancing with Azure Front Door
To provide global high availability and efficient traffic distribution, Azure Front Door (AFD) can be implemented as the global load balancer. AFD ensures that users are routed to the nearest and healthiest backend, reducing latency and improving redundancy. It supports automatic failover between regions, ensuring seamless service availability even in the event of failures.
Regional Load Balancing with Azure Application Gateway
For regional traffic management, Azure Application Gateway can be set up in front of backend services. It provides layer-7 load balancing, Web Application Firewall (WAF) protection, and supports SSL termination to secure communication between users and backend services. It also enables URL-based routing and session affinity, ensuring efficient distribution of requests across multiple instances.
Virtual Network (VNet) and Subnet Architecture
To achieve better security and network segmentation, an Azure Virtual Network (VNet) can be created with multiple public and private subnets.
For effective management, it is recommended to:
- Use public subnets for the Application Gateway.
- Use private subnets for worker nodes and databases
- Configure Network Security Groups (NSGs) to allow only necessary traffic, enhancing security.
- To enable secure and scalable outbound internet connectivity for resources in private subnets, a NAT Gateway can be deployed. NAT Gateway provides:
- Static outbound IP addresses: Ensures predictable and secure outbound traffic.
- Scalability: Handles thousands of outbound connections simultaneously.
Private Container Registry for Secure Image Storage
To store and manage container images securely, Azure Container Registry (ACR) with private access can be used.
This ensures that only authorized services can pull images from the registry, reducing security risks. ACR also supports image scanning and integration with CI/CD pipelines to automate deployments.
Kubernetes Cluster with Autoscaling
A key part of the infrastructure is Azure Kubernetes Service (AKS) with cluster autoscaling enabled, ensuring that clusters dynamically scale based on resource demand while maintaining cost efficiency. We also enable horizontal pod autoscaling which allows applications to scale based on CPU and memory utilization.
Secure Secrets Management with Azure Key Vault
To securely manage sensitive information such as database credentials and API keys, we use Azure Key Vault with network restrictions. Access to secrets should be limited to selected trusted networks which helps minimize attack vectors. Additionally, RBAC-based access control can be implemented to restrict unauthorized access.
High Availability Database Deployment
Azure Database for PostgreSQL and MySQL can be used to provide managed database solutions with built-in high availability, automatic backups, and scaling capabilities.
For NoSQL database requirements, Azure Cosmos DB can be considered as an alternative to MongoDB.
It provides:
- Multi-Model Support: Supports document (MongoDB API), key-value, graph, and column-family data models
- Global Distribution: Ensures low latency and high availability with multi-region writes
- Automatic Scaling: Dynamically adjusts throughput based on application needs
- Built-in Security: Offers data encryption at rest and in transit
However, if cost is a concern, hosting MongoDB on an Azure Virtual Machine (VM) in a private subnet is a cost-effective alternative.
To ensure database availability:
- Replica sets can be configured to provide failover
- Azure Bastion Host can be used for secure remote access to the VM
- Automated backup policies can be implemented to safeguard data.
Backup and Disaster Recovery with Azure Recovery Vault
To protect against accidental deletions or data corruption, Azure Recovery Services Vault can be implemented with the following configurations:
- Soft Delete Enabled: Ensures that backups remain available for 14 days after deletion.
- Geo-Redundant Backup: Stores copies in multiple regions for added resilience.
- Incremental backups can be configured to optimize storage and cost.
Comprehensive Monitoring with Azure Monitoring Tools
Azure provides several monitoring and logging tools to ensure application and infrastructure observability:
- Azure Monitor: Provides end-to-end observability across Azure resources, applications, and networks
- Azure Log Analytics: Collects and analyzes logs from different Azure services, allowing for detailed query-based insights
- Azure Application Insights: Helps in monitoring application performance, tracking dependencies, and diagnosing issues in real-time
- Azure Managed Prometheus and Grafana: Used for real-time insights, dashboards, and alerting mechanisms, ensuring proactive issue resolution and performance tracking
These tools help in optimizing infrastructure performance, troubleshooting issues, and gaining deeper insights into resource utilization.
Optimizing Performance with Azure Cache for Redis
To enhance application performance and reduce database load, Azure Cache for Redis can be integrated between the application (running in Kubernetes) and with the wide variety of databases. This enables caching frequently accessed data, reducing query times, and improving response speeds.
How It Works in This Setup
- Kubernetes applications first check Redis Cache for frequently accessed data.
- If the data is available in Redis (cache hit), it is returned immediately, reducing database load.
- If the data is not available in Redis (cache miss), the application queries MongoDB, retrieves the data, and then stores it in Redis for future requests.
Benefits of Using Azure Redis Cache
- Faster Response Times – Frequently accessed queries are served instantly from memory
- Reduced Database Load – MongoDB will handle fewer requests, improving scalability
- High Availability – Azure Redis Cache supports replication and failover
- Supports Pub/Sub Messaging – Helps in real-time event-driven applications
Flexible Data Expiry – You can configure time-to-live (TTL) for cached data
Diagnosing Network Issues with Azure Network Watcher
For better network troubleshooting and diagnostics, Azure Network Watcher can be implemented.
It helps in analyzing:
- IP Flow to check if traffic is being allowed or denied
- Packet Capture for in-depth network traffic analysis
- Next Hop to determine network route troubleshooting
Connection Troubleshooting to identify network bottlenecks
Governance and Compliance with Azure Policy
To enforce organizational standards and compliance, Azure Policy can be implemented.
Azure Policy provides:
- Policy definitions: Enforce rules for resource configurations (e.g., requiring encryption for storage accounts)
- Compliance monitoring: Tracks adherence to organizational policies
Automated remediation: Automatically corrects non-compliant resources
Tools Used in This Infrastructure
This setup utilizes several Azure services to ensure high availability, scalability, security, and performance:
- Azure Front Door – Global load balancing and high availability
- Azure Application Gateway – Regional load balancing with WAF protection
- Azure Kubernetes Service (AKS) – Managed Kubernetes with autoscaling
- Azure Container Registry (ACR) – Secure storage for container images
- Azure Key Vault – Secure secrets management
- Azure Virtual Network (VNet) with Subnets – Network segmentation and isolation
- Azure Network Security Groups (NSGs) – Control and restrict traffic between services
- Azure Cosmos DB – Fully managed NoSQL database with global distribution
- Azure Virtual Machines (VMs) – Hosting alternative for MongoDB with replication
- Azure Bastion Host – Secure remote access to VMs in private subnets
- Azure Recovery Services Vault – Backup and disaster recovery
- Azure Monitor – End-to-end observability for Azure resources
- Azure Log Analytics – Centralized log collection and analysis
- Azure Application Insights – Real-time application performance monitoring
- Azure Managed Prometheus & Grafana – Monitoring and alerting for Kubernetes and VMs
- Azure Cache for Redis – Caching layer to improve application performance
- Azure Network Watcher – Network monitoring and troubleshooting
- Microsoft Defender for Cloud – Security monitoring and threat detection
Azure Policy – Governance and compliance enforcement
Conclusion
By leveraging Azure’s comprehensive suite of services, a highly available, scalable, and secure infrastructure can be built. This architecture ensures fault tolerance, automated recovery, and optimal performance for modern cloud applications. The tools and services, mentioned above, seamlessly work together to provide a robust foundation for your cloud-native workloads.
As your infrastructure continues to evolve, take it a step further by integrating these configurations into your CI/CD pipelines. Codify reliability and security as part of your deployment strategy and as ongoing engineering practices. With the right foundation in place, you can confidently build systems that are resilient, secure, and ready to scale with your needs.

