GitHub Supply Chain Attack

Naren Ravilla
Founder & CEO
Introduction
GitHub supply chain attacks occur when attackers compromise open-source projects by injecting malicious code. This code then spreads to other projects and organizations that rely on these repositories, leading to potential data breaches, malware infections, and unauthorized access.
Incident Overview
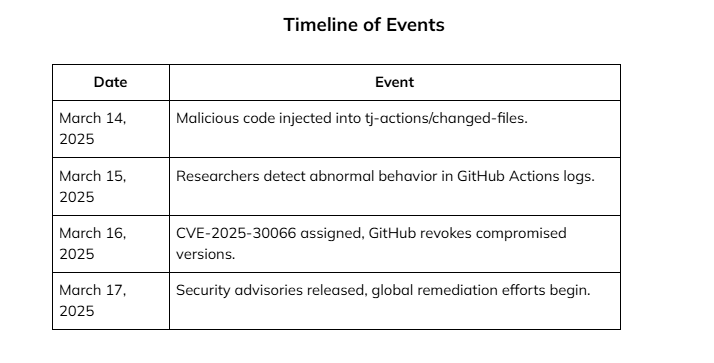
On March 14, 2025, a major supply chain attack targeted the tj-actions/changed-files GitHub Action, affecting multiple repositories worldwide. The attacker injected malicious code into the action’s repository, exposing secrets and environment variables used in CI/CD workflows. This has been identified as CVE-2025-30066.
Key Risks:
- Credential Leakage: API keys, OAuth tokens, and database credentials were exposed in public logs.
- Code Integrity Threats: Compromised workflows may have executed malicious commands.
- Compliance Impact: Potential violations of ISO 27001, SOC 2, and GDPR.
Incident Detection and Response:
✔ Compromised versions (v1 – v45.0.7) identified and quarantined.
✔ Impacted repositories scanned for leaked credentials.
✔ Vulnerable GitHub Actions upgraded to version 46+.
✔ Secrets rotated, revoked, and reissued.
✔ Security monitoring and auditing tools deployed to detect anomalies.
Attack Analysis
AI is transforming NOC and SOC operations by enhancing efficiency, accuracy, and scalability, enabling organizations to manage complex environments with greater precision. However, while AI-driven automation offers significant benefits, integrating it into existing systems comes with its own challenges.
Organizations must navigate complexities such as infrastructure adjustments, data quality concerns, and skill gaps to fully leverage AI’s potential. By understanding both the benefits and challenges of AI integration, businesses can develop strategic approaches to maximize its value while mitigating potential risks.
Root Cause:
- An attacker gained access to a GitHub Personal Access Token (PAT) with admin privileges on the tj-actions/changed-files repository.
- The token was used to modify the GitHub Action code, injecting malicious scripts into multiple releases.
- Secrets stored in GitHub Actions workflows were extracted and leaked via encoded payloads in workflow logs.
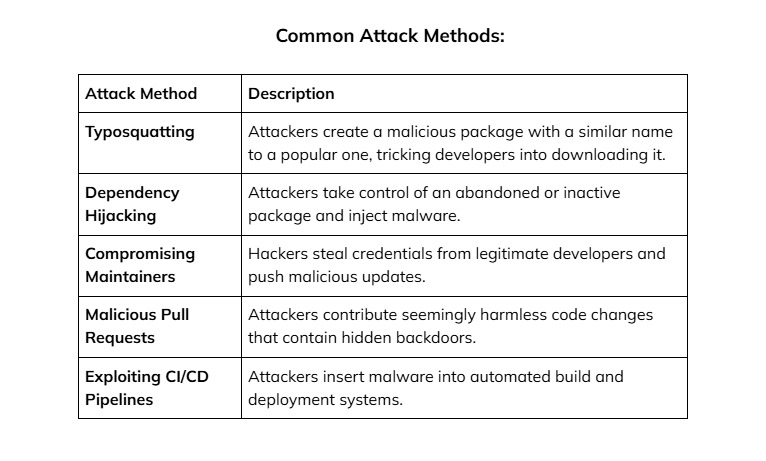
How Do GitHub Supply Chain Attacks Happen?
Attackers use various methods to introduce malicious code into open-source projects.
These include:
Can Anyone Push Malicious Code to Open-Source Projects?
Not exactly. Open-source projects on GitHub have different permission levels:
- Public repositories: Anyone can fork and propose changes, but only maintainers can merge them.
- Private repositories: Only authorized users can modify code.
- Package registries (e.g., npm, PyPI, Maven): Developers can publish libraries, but security measures vary.
Despite these protections, attackers exploit human errors, outdated software, and social engineering tactics to gain access.
Impact on Our Customers
Organizations using open-source dependencies are at risk if:
- They use unverified or outdated dependencies.
- They do not check for updates and security advisories.
- Their CI/CD pipelines do not validate dependencies before deploying applications.
They fail to use tools like GitHub Dependabot or software composition analysis (SCA) to detect malicious dependencies.
Risk Levels Based on Security Posture:
High Risk:
- Uses unverified third-party dependencies.
- No security scans in CI/CD pipelines.
- Lack of dependency monitoring tools.
- Uses outdated or abandoned packages.
- No code review for external contributions.
Medium Risk:
- Uses dependencies from partially trusted sources.
- Some security scans are implemented but not enforced.
- Dependency monitoring is limited.
- Uses some outdated packages but has mitigations.
- Reviews external contributions inconsistently.
Low Risk:
- Uses only verified and trusted dependencies.
- CI/CD pipelines enforce strict security scans.
- Dependency monitoring tools are actively used.
- No outdated or abandoned packages are in use.
- Strict code review policies for external contributions.
If three or more high risk factors are present, the likelihood of an attack is high.
How to Detect and Prevent GitHub Supply Chain Attacks
Detection Methods:
- Monitor Repository Activity: Look for unusual commits or dependency changes.
- Check for Typosquatted Packages: Verify package names before installing.
- Review Pull Requests Carefully: Ensure code changes do not introduce malicious functions.
- Analyze Dependencies: Use security tools to scan for vulnerabilities.
Preventive Measures:
- Use GitHub Dependabot to track dependency updates.
- Implement code signing for software releases.
- Require multi-factor authentication (MFA) for repository maintainers.
- Use software composition analysis (SCA) tools to verify open-source components.
- Limit third-party dependencies to trusted sources.
- Enable branch protection rules to prevent unauthorized code changes.
Real-World Example: The Event-Stream Attack
One of the most infamous GitHub supply chain attacks was the Event-Stream incident (2018):
- A popular npm package, Event-Stream, had over 2 million weekly downloads.
- The original maintainer transferred ownership to a new contributor.
- The new owner added malicious code to steal cryptocurrency wallets.
- Thousands of applications unknowingly included the compromised package.
- The malware was discovered months later, after users reported suspicious activity.
This attack highlights the risks of blindly trusting open-source dependencies and the importance of continuous monitoring.
Conclusion
To protect against GitHub supply chain attacks, organizations must:
- Verify and assess open-source dependencies before use.
- Implement security controls in CI/CD pipelines.
- Use automated tools to detect vulnerabilities.
- Educate developers on secure coding practices.
By following these measures, we can minimize the risk of supply chain attacks and safeguard our customers from potential threats.

