
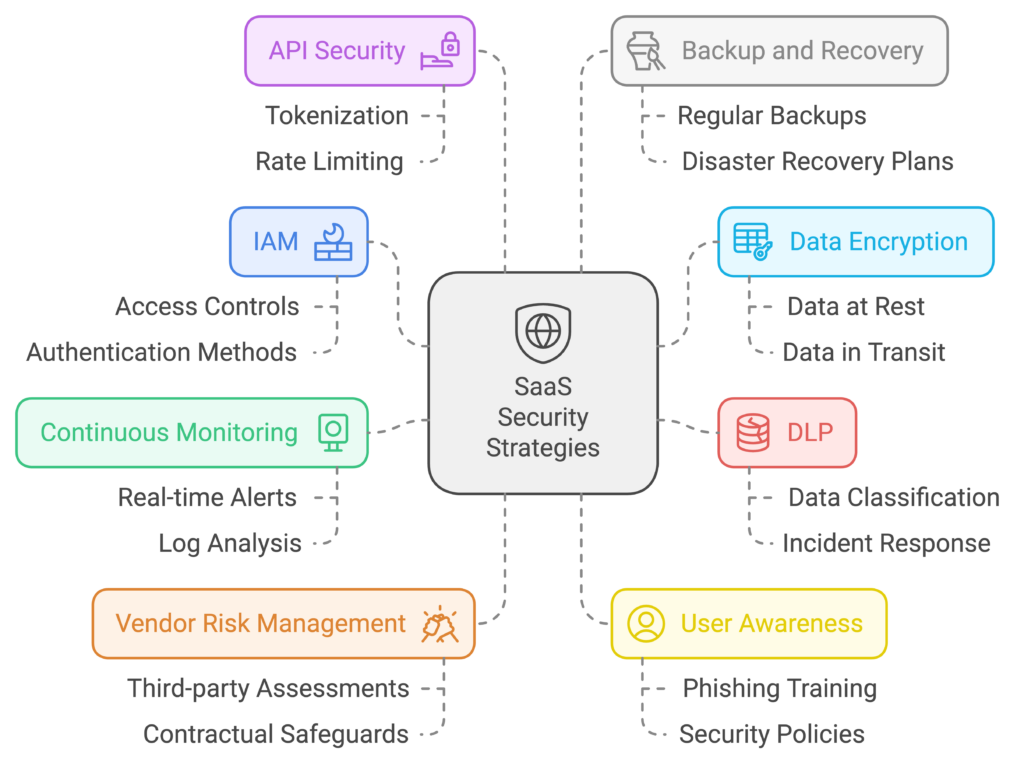
8 Essential Steps to Strengthen Your SaaS Security

Naren Ravilla
Founder & CEO
Introduction
The rapid adoption of SaaS applications has brought incredible flexibility and scalability to businesses, but it has also introduced new security risks. From data breaches to insider threats, SaaS applications face a range of challenges that require robust security measures.
Below are eight of the most effective ways to bolster SaaS security and protect your organization from emerging threats.
1. Identity and Access Management (IAM)
2. Data Encryption
3. Data Loss Prevention
4. Continuous Monitoring and Logging
5. Vendor Risk Management
6. User Awareness and Training
7. API Security
8. Backup and Recovery
Identity and Access Management (IAM): Safeguard Entry Points
Ensuring only authorized users can access your SaaS applications is fundamental to security. Identity and Access Management (IAM) is crucial in verifying user identities, managing access privileges, and enforcing secure authentication.
- Multi-Factor Authentication (MFA): Adding an extra layer of verification ensures that unauthorized access remains challenging even if a password is compromised. MFA combines factors like a password, a smartphone, or biometrics to secure access. According to Microsoft, MFA can prevent up to 99.9% of account compromise attacks by adding a second layer of defense beyond passwords alone.
- Single Sign-On (SSO): With SSO, employees use one set of credentials for multiple applications, reducing password fatigue and strengthening security. A study by LastPass found that companies using SSO experienced half as many login-related security incidents compared to those that did not use SSO, reducing the risk of password-related breaches.
Data Encryption: Securing Your Information at Every Stage
Data encryption protects sensitive information during transfer (in transit) and storage (at rest), minimizing exposure risk. With a ten percent increase from 2023 in global average cost of data breaches, encryption is ever more important in protecting sensitive data and information.
- Encryption in Transit and at Rest: Encrypting data (in transit) protects it during its journey across networks, while encryption (at rest) secures data stored within SaaS applications. By encrypting data, companies reduce the risk of unauthorized access and data leaks.
- Key Management: Effective encryption requires proper key handling. Using key management solutions, either third-party or native to the application, ensures secure rotation, revocation, and reduces compromise risks. Automating key management helps you streamline encryption processes and further strengthen security.
Data Loss Prevention (DLP): Controlling Sensitive Data Exposure
Data Loss Prevention (DLP) tools prevent accidental or intentional exposure of sensitive information. DLP protects intellectual property and helps ensure regulatory compliance with GDPR, HIPAA, and CCPA. Non-compliance with regulations such as GDPR or HIPAA has led to fines exceeding $1 billion in the past year alone, highlighting the importance of DLP for compliance and avoiding costly penalties.
- Monitor Data Transfers: DLP tools enable the monitoring of data flow, tracking where data is stored, accessed, and shared within SaaS applications. This monitoring capability helps detect unusual activity, like unauthorized sharing of sensitive data, in real time.
- DLP Policies: By defining specific policies around data handling, you can better protect intellectual property and other sensitive information. DLP policies also help identify anomalous behaviors, which can signal a potential breach.
Continuous Monitoring and Logging: Always Be Watching
Constant monitoring of application activity enables your security team to proactively detect and respond to threats. Organizations with real-time monitoring and logging reduce the time to identify and contain breaches by up to 43% compared to those without proper monitoring. Reducing your response time is crucial not only for minimizing damage and costs associated with a breach but also for building resilience.
- Enable Detailed Logs: Capturing comprehensive logs of actions—such as login attempts, file access and configuration changes—provides valuable information for threat detection and incident response.
- SIEM solutions (Security Information and Event Management): SIEM tools analyze log data across multiple sources, helping organizations identify unusual behaviors or breaches. SIEMs centralize alerts and reports, streamlining incident detection and response.
Vendor Risk Management: Trust, But Verify
With SaaS applications managed by third-party vendors, it’s critical to ensure these vendors meet stringent security standards. A robust vendor risk management program is key to safeguarding your data and maintaining compliance.
- Vendor Compliance: Ensure SaaS providers meet recognized standards like SOC 2, ISO 27001, and other certifications, indicating they follow best practices in security and data protection.
- Regular Audits: Perform periodic security assessments on vendors to ensure they meet your organization’s evolving security needs. Regular audits validate that vendors remain compliant and continue to uphold your security requirements.
User Awareness and Training: The Human Element
A well-informed workforce is essential to safeguarding SaaS applications, as human error is often the weakest link in security.
- Phishing Simulations: Conduct regular phishing tests to train employees on recognizing and reporting suspicious emails. Phishing simulations also provide insight into how vulnerable your organization may be to social engineering threats.
- Periodic Training: Provide ongoing training covering account security, data handling, and incident reporting. Employees should be able to recognize signs of a potential breach and understand the importance of responsible data usage.
API Security: Lock Down Integration Points
APIs facilitate integrations between SaaS applications, allowing data exchange and functionality sharing. However, improperly secured APIs can be a major vulnerability.
- Secure APIs: Implement strong authentication and encryption for all API traffic. This helps prevent unauthorized access to sensitive data through exposed endpoints.
- Monitoring and Rate Limiting: Monitor API activity for unusual patterns and limit the number of requests to prevent abuse. Rate limiting prevents Denial of Service (DoS) attacks by ensuring systems are not overwhelmed by traffic.
Backup and Recovery: Prepare for the Unexpected
While prevention is the first line of defense, recovery ensures resilience against data loss. Implementing a sound backup and recovery strategy helps protect your SaaS applications from accidental deletions, malicious attacks, and system failures.
- Automated Backups: Regular backups of critical SaaS data allow for data recovery after a cyberattack or accidental data deletion. Automating backups minimizes the chance of human error.
- Testing Recovery: Test your backups periodically to verify that data can be restored accurately and swiftly. Regular testing ensures the reliability of your backup solution and verifies data integrity.
SaaS Security Strategies
Conclusion
Securing SaaS applications is essential as organizations move increasingly toward cloud-based tools. Implementing these eight strategies will lay a strong foundation for SaaS security, equipping your organization to face today’s threats. While technology plays a major role in security, effective SaaS protection combines technical solutions with vendor management, employee education, and a commitment to continuous improvement. By taking these steps, you’ll be well on your way to creating a safer SaaS environment for your business.
Prokopto specializes in helping SaaS companies implement these critical security measures through tailored solutions that prioritize compliance, scalability, and operational excellence, ensuring your organization stays protected in a rapidly evolving threat landscape.

